Problem
Managing multiple self-hosted services across different networks traditionally requires complex networking configurations—including static IPs, port forwarding, and dynamic DNS. For a personal developer environment that spans laptops, old machines, and mobile clients, this quickly becomes unmanageable and insecure. I needed a solution to simplify connectivity, ensure privacy, and centralize access control across distributed hardware.
Solution
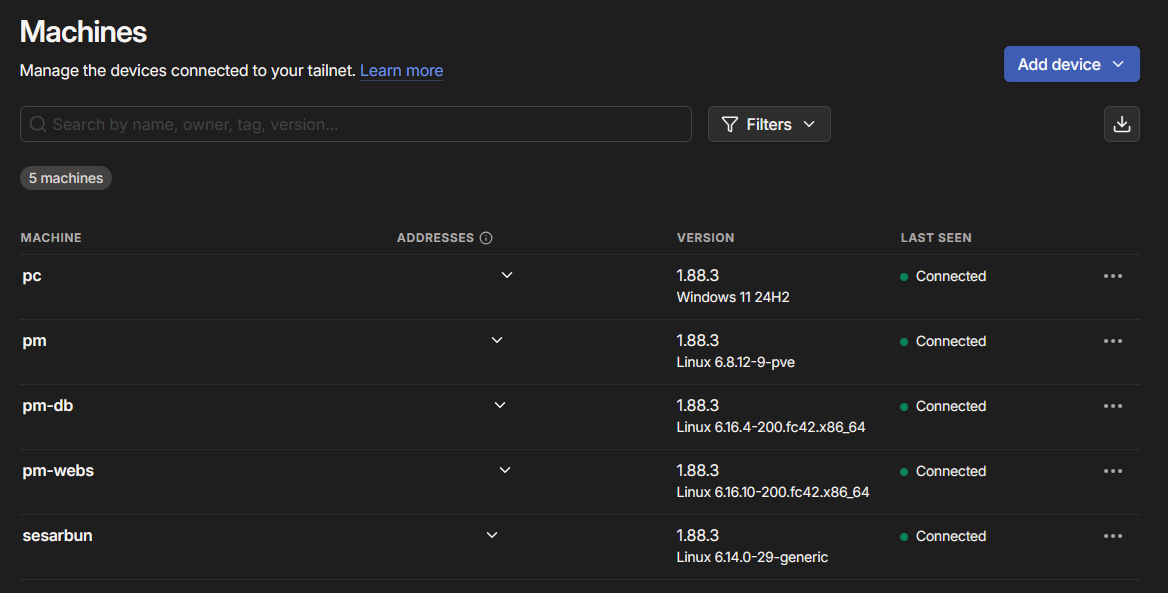
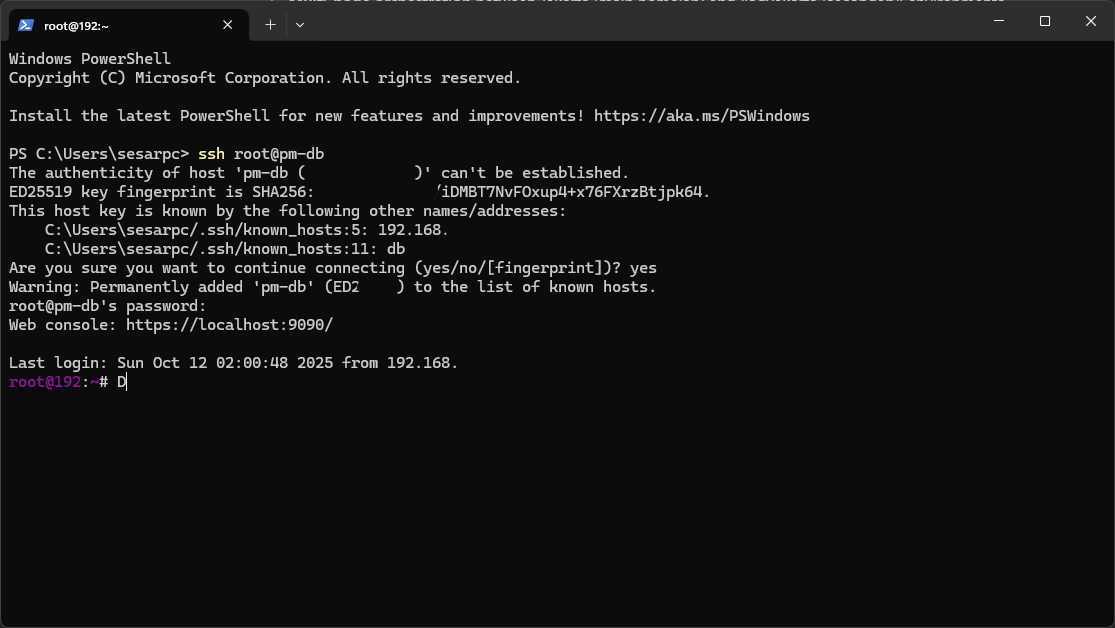
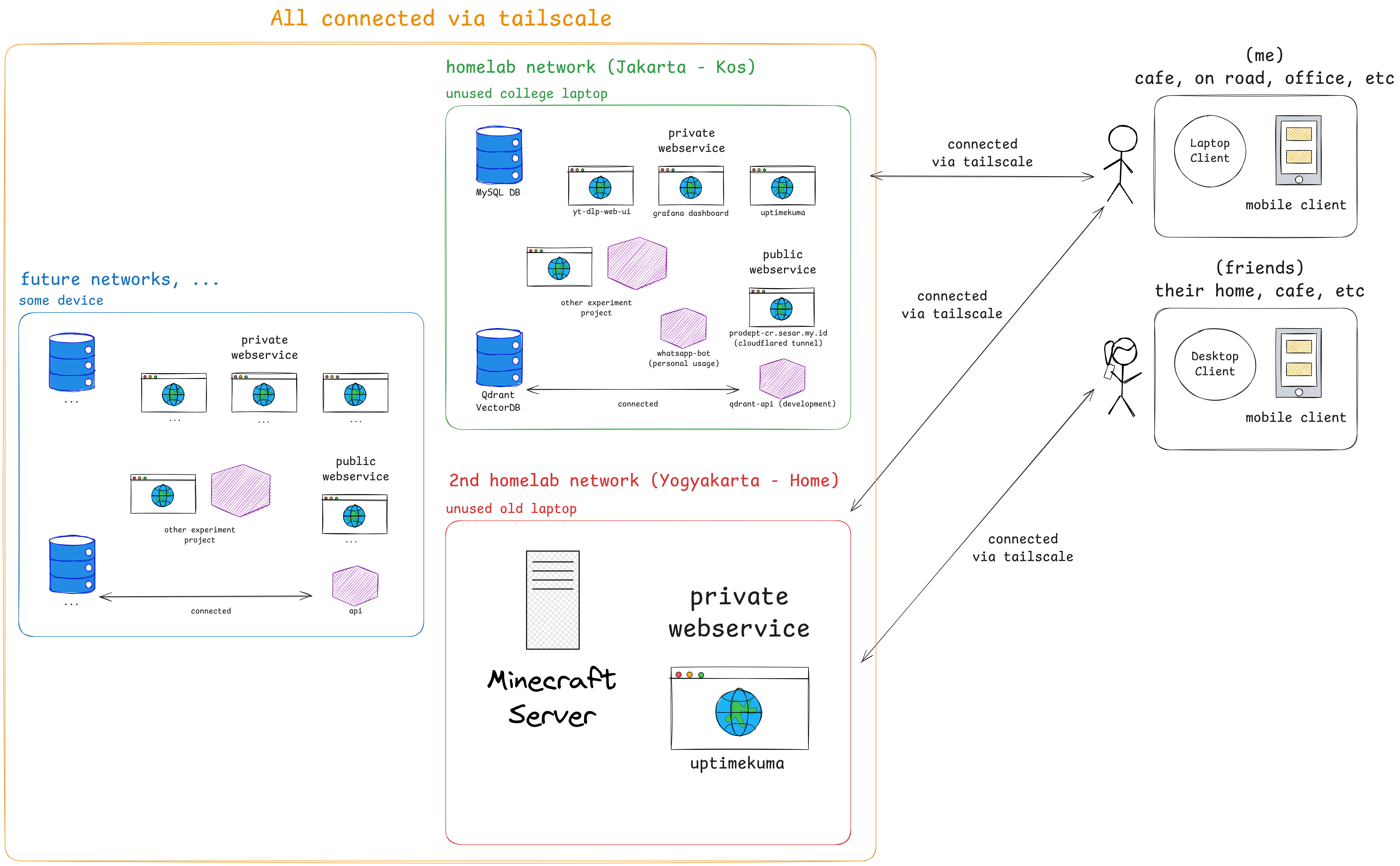
Using Tailscale, I created a peer-to-peer mesh VPN connecting all homelab devices, clients, and potential future nodes under a single virtual network. Each machine—from old laptops repurposed as servers to mobile clients—joins the network automatically and can securely communicate using internal IPs.
- The Jakarta node hosts MySQL, Qdrant VectorDB, Grafana dashboards, and experimental services.
- The Yogyakarta node runs uptime monitoring and a Minecraft server for local projects.
- Clients (laptop and mobile) can access any internal web service privately through Tailscale IPs.
- Cloudflare tunnels handle selective public exposure of specific APIs while maintaining security boundaries.
tldr
- Situation: Two homelabs in different cities, both running separate services.
- Task: Connect them securely without relying on public IP exposure or manual VPN configuration.
- Action: Deployed Tailscale on all nodes, configured subnet routing, and integrated private/public service layers.
- Result: Achieved secure, frictionless access to all self-hosted services from anywhere, with minimal latency and zero manual VPN maintenance.
Technical Highlights
- Tailscale for device identity management and WireGuard-based encryption.
- Qdrant VectorDB for semantic data storage across distributed hosts.
- Cloudflare Tunnel for exposing selected web services securely to the internet.
- Grafana + Uptime Kuma for network and uptime monitoring.
- Multi-node orchestration between Jakarta (main homelab) and Yogyakarta (secondary) environments.
- Zero-trust architecture: Each device authenticates through Tailscale’s coordination server, eliminating shared keys or static VPN credentials.
Reflection
This setup demonstrates how modern self-hosting can scale securely and globally with minimal infrastructure overhead. Tailscale transformed my fragmented devices into a cohesive private cloud, bridging geographic boundaries effortlessly. The experience reinforced the value of designing modular, resilient homelabs—where every node, from a repurposed laptop to a new experimental device, can join the ecosystem securely in minutes.
There were so much feature in the tailscale, such as managing permissions, access controls, view the logs, add, monitor services, etc. But for me, this is personally enough for now.
Gallery